|
TCP -
Connection Oriented Protocol
The
Sequence and Acknowledgement fields are two of the
many features that help us classify TCP as a
connection oriented protocol. As such, when data is
sent through a TCP connection, they help the remote
hosts keep track of the connection and ensure that
no packet has been lost on the way to its
destination.
TCP
utilizes positive acknowledgments, timeouts and
retransmissions to ensure error-free, sequenced
delivery of user data. If the retransmission timer
expires before an acknowledgment is received, data
is retransmitted starting at the byte after the last
acknowledged byte in the stream.
A
further point worth mentioning is the fact that
Sequence numbers are generated differently on each
operating system. Using special algorithims (and
sometimes weak ones), an operating system will
generate these numbers, which are used to track the
packets sent or received, and since both Sequence
and Acknowledgement fields are 32bit, there are
2^32= 4,294,967,296 possibilities of generating a
different number!
Initial Sequence Number (ISN)
When
two hosts need to transfer data using the TCP
transport protocol, a new connection is created.
This involves the first host that wishes to initiate
the connection, to generate what is called an
Initial Sequence Number (ISN), which is basically
the first sequence number that's contained in the
Sequence field we are looking at. The ISN has always
been the subject of security issues, as it seems to
be a favourite way for hackers to 'hijack' TCP
connections.
Believe
it or not, hijacking a new TCP connection is
something an experienced hacker can alarmingly
achieve with very few attempts. The root of this
security problem starts with the way the ISN is
generated.
Every
operating system uses its own algorithm to generate
an ISN for every new connection, so all a hacker
needs to do is figure out, or rather predict, which
algorithm is used by the specific operating system,
generate the next predicted sequence number and
place it inside a packet that is sent to the other
end. If the attacker is successful, the receiving
end is fooled and thinks the packet is a valid one
coming from the host that initiated the connection.
At the
same time, the attacker will launch a flood attack
to the host that initiated the TCP connection,
keeping it busy so it won't send any packets to the
remote host with which it tried to initiate the
connection.
Here is
a brief illustration of the above-mentioned attack:
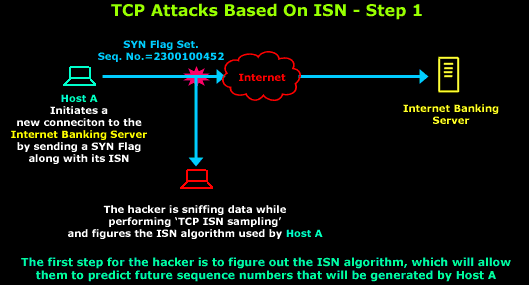
As
described, the hacker must find the ISN algorithm by
sampling the Initial Sequence Numbers used in all
new connections by Host A.
Once this is complete and the hacker knows the
algorithm and they are ready to initiate their
attack:
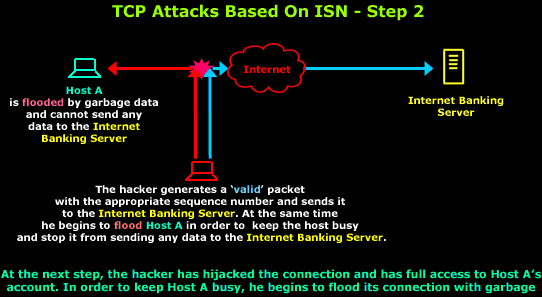
Timing
is critical for the hacker, so he sends his first
fake packet to the Internet
Banking Server while at the same time starts
flooding
Host A with garbage
data in order to consume the host's bandwidth and
resources. By doing so, Host A
is unable to cope with the data it's receiving and
will not send any packets to the
Internet Banking Server.
The
fake packet sent to the
Internet Banking Server will contain valid
headers, meaning it will seem like it originated
from Host A's IP
Address and will be sent to the correct port the
Internet Banking Server
is listening to.
There
have been numerous reports published online that
talk about the method each operating system uses to
generate its ISN and how easy or difficult it is to
predict. Do not be alarmed to discover that the
Windows operating system's ISN algorithm is by far
the easiest to predict!
Programs such as 'nmap' will actually test to see
how difficult it can be to discover the ISN
algorithm used in any operating system. In most
cases, hackers will first sample TCP ISN's from the
host victim, looking for patterns in the initial
sequence numbers chosen by TCP implementations when
responding to a connection request. Once a pattern
is found it's only a matter of minutes for
connections initiated by the host to be hijacked.
Example of Sequence and Acknowledgment
Numbers
To help
us understand how these newly introduced fields are
used to track a connection's packets, an example is
given below.
Before
we proceed, we should note that you will come across
the terms "ACK flag" or "SYN flag"; these terms
should not be confused with the Sequence and
Acknowledgment numbers as they are different fields
within the TCP header. The screen shot below is to
help you understand:
|
