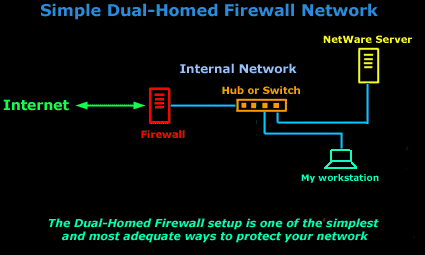
Firewall TopologiesIntroductionIn this section we are going to talk about the different ways a firewall can be set up. Depending on your needs, you can have a very simple firewall setup which will provide enough protection for your personal computer or small network, or you can choose a more complicated setup which will provide more protection and security. Let's have a look starting from the simple solutions, and then move on to the more complicated ones. Just keep in mind we are not talking about a firewall which is only a piece of software which runs on the same computer you use to connect to the internet and do your work, but we are talking about a physical computer which is a dedicated firewall.A Simple Dual-Homed Firewall The dual-homed firewall is one of the simplest and possibly most common way to use a firewall. The Internet comes into the firewall directly via a dial-up modem (like me :) ) or through some other type of connection like an ISDN line or cable modem. You can't have a DMZ (See the DMZ page for more info) in this type of a configuration.
A Two-Legged Network with a full exposed DMZ In this more advanced configuration, shown in the picture below, the router that connects to the outside work is connected to a hub (or switch).
Machines that want direct access to the outside world, unfiltered by the firewall, connect to this hub. One of the firewall's network adapters also connects to this hub. The other network adapter connects to the internal hub. Machines that need to be protected by the firewall need to connect to this hub. Any of these hubs could be replaced with switches for added security and speed, and it would be more effective to use a switch for the internal hub. There are good things about the exposed DMZ configuration. The firewall needs only two network cards. This simplifies the configuration of the firewall. Additionally, if you control the router you have access to a second set of packet-filtering capabilities. Using these, you can give your DMZ some limited protection completely separate from your firewall. On the other hand, if you don't control the router, your DMZ is totally exposed to the Internet. Hardening a machine enough to live in the DMZ without getting regularly compromised can be tricky. The exposed DMZ configuration depends on two things: 1) an external router, and 2) multiple IP addresses. If you connect via PPP (modem dial-up), or you don't control your external router, or you want to masquerade your DMZ, or you have only 1 IP address, you'll need to do something else.There are two straightforward solutions to this, depending on your particular problem.
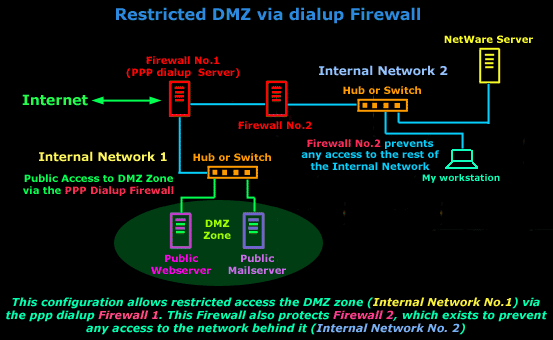
One solution is to build a second router/firewall. This is useful if you're connecting via PPP. One machine is the exterior router/ firewall (Firewall No.1). This machine is responsible for creating the PPP connection and controls the access to our DMZ zone. The other firewall (Firewall No.2) is a standard dual-homed host just like the one we spoke about at the beginning of the page, and its job is to protect the internal network. This is identical to the situation of a dual homed firewall where your PPP machine is the local exterior router. The other solution is to create a three-legged firewall, which is what we are going to talk about next.
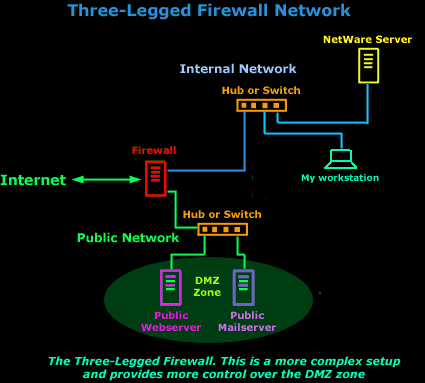
The Three-legged firewall This means you need an additional network adapter in your firewall box for your DMZ. The firewall is then configured to route packets between the outside world and the DMZ differently than between the outside world and the internal network. This is a useful configuration, and I have seen many of our customers using it.
The three-legged setup can also give you the ability to have a DMZ if you're stuck with the simple topology outlined first (dual homed firewall). Replace "router" with "modem," and you can see how this is similar to the simple topology (dual homed firewall), but with a third leg stuck on the side :) If you're being forced or have chosen to IP masquerade, you can masquerade the machine or machines in the DMZ too, while keeping them functionally separate from protected internal machines. People who have cable modems or static PPP connections can use this system to run various servers within a DMZ as well as an entire internal network off a single IP address. It's a very economic solution for small businesses or home offices. The primary disadvantage to the three-legged firewall is the additional complexity. Access to and from the DMZ and to and from the internal network is controlled by one large set of rules. It's pretty easy to get these rules wrong if you're not careful ! On the other hand, if you don't have any control over the Internet router, you can exert a lot more control over traffic to and from the DMZ this way. It's good to prevent access into the DMZ if you can. And I think that just about completes our discussion of Firewall Topologies ! |
||
| TOP | ||