|
The best thing you can
do to "see" it yourself is to grab a packet sniffer
which you will conveniently find in our download
section and try to capture a few packets while
you're ftp'ing to a site.
Both
Ports - 20 and
21 -
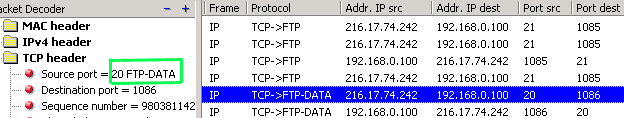
Active FTP Mode
I have included a
screenshot from my workstation which clearly shows
the 2 ports used. In the example, I have ftp'ed into
ftp.cdrom.com. Please
click here to view the full picture
Only Port 21 - Passive FTP Mode
Now, in the next
picture I ftp'ed into my NetWare server here at home
and guess what .... Only Port
21 was used ! Here is the screen shot:
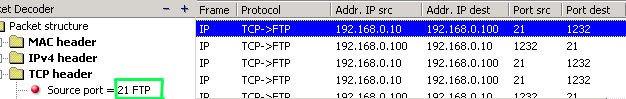
Please
click here to view the full picture.
Let
me explain why this is happening:
FTP has two separate
modes of operation: Active
and Passive. You will
use either one depending on whether your PC is
behind a firewall.
Active Mode FTP
Active mode is
usually used when there isn't any firewall between
you and the FTP server. In such cases you have a
direct connection to the Internet. When you (the
client) try to establish a connection to a
FTP server, your
workstation includes a second port number (using the
PORT command) that is
used when data is to be exchanged, this is known as
the Data Channel.
The
FTP server then starts
the exchange of data from its own
port 20 to whatever
port was designated by your workstation (in the
screen shot, my workstation used port 1086), and
because the server initiated the communication, it's
not controlled by the workstation client. This can
also potentially allow uninvited data to arrive to
your computer from anywhere posing as a normal
FTP transfer. This is
one of the reasons Passive FTP
is more secure.
Passive Mode FTP
Using normal or
passive FTP, a client
begins a session by sending a request to communicate
through TCP port 21,
the port that is conventionally assigned for this
use at the FTP server.
This communication is known as the Control Channel
connection.
At this point, a
PASV command is sent
instead of a PORT
command. Instead of specifying a port that the
server can send to, the PASV
command asks the server to specify a port it wishes
to use for the Data Channel connection. The server
replies on the Control Channel with the port number
which the client then uses to initiate an exchange
on the Data Channel. The server will thus always be
responding to client-initiated requests on the Data
Channel and the firewall can correlate these.
It's simple to
configure your client FTP program to use either
Active or
Passive
FTP. For example, in
Cute FTP, you can set your program to use Passive
FTP by going to FTP--> Settings --> Options and then
selecting the "Firewall" tab :
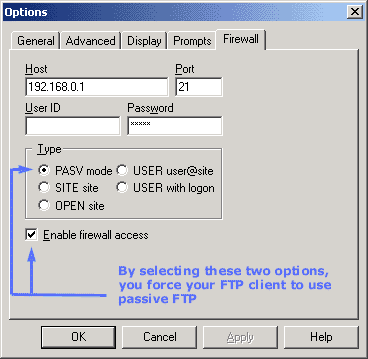
If you remove the
above options, then your workstation will be using
(if possible) Active FTP mode,
and I say "if possible" cause if your already behind
a firewall, there is probably no way you will be
using Active FTP, so
the program will automatically change to
Passive FTP mode.
So let's have a look
at the process of a computer establishing an
FTP connection with a
server: .
........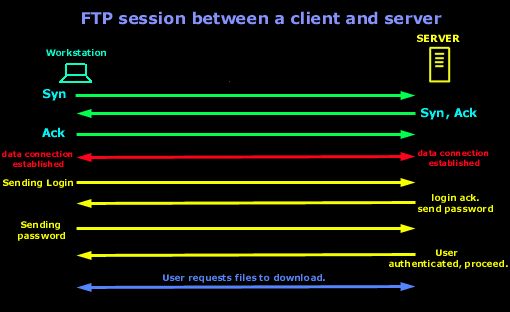 .......... ..........
The above is assuming
a direct connection to the FTP server. For
simplicity reasons, we are looking at the way the
FTP connection is created and not worring if it's a
Passive or Active FTP connection. Since FTP is using
TCP as a transport, you would expect to see the
3-way handshake. Once
that is completed and there is
data connection established, the client will
send its login name and then password. After the
authentication sequence
is finished and the user is authenticated to the
Server, it's allowed access and is ready to
leach the site dry :)
Finally, below are the most commonly used FTP
commands:
ABOR: abort previous
FTP command
LIST and NLST: list
file and directories
DELE: delete a file
RMD: remove a
directory
MKD: create a
directory
PWD: print current
working directory ( show you which dir. your at)
PASS: send password
PORT: request open
port number on specific IP address/port number
QUIT: log off from
server
RETR: retrieve file
STOR: send or put
file
SYST: identity system
type
TYPE: specify type (A
for ASCII, I for binary)
USER: send username
And that just about
complete's our analysis on the FTP protocol ! |
