DNS Query Message Format
Introduction
This
section will deal with the analysis of the DNS
packets. This will allow us to see the way DNS
messages are formatted and the options and variables
they contain. To understand a protocol, you must
understand the information the protocol carries from
one host to another.
Because
the DNS message format can vary, depending on the
query and the answer, I've broken this analysis into
two parts. Part 1
analyses the DNS format
of a query, in other
words, it shows how the packet looks when we ask a
DNS server to resolve a domain.
Part 2 analyses the DNS
format of an answer, where the
DNS server is
responding to our query.
I find
this method more informative and easy to understand
rather than combining the analysis of queries and
answers.
DNS Analysis - Host Query
As
mentioned in the previous sections of the DNS
Protocol, a DNS query
is generated when the client needs to resolve a
domain name into an IP Address. This could be the
result of entering "www.firewall.cx"
in the url field of your web browser, or simply by
launching a program that uses the Internet and
therefore generates DNS
queries in order to successfully communicate
with the host or server it needs.
Now, I've
also included a live example (using my packet
analyser), so you can compare theory with practice
for a better understanding. After this we will have
a look at the meaning of each field in the packet,
so let's check out what a packet containing a
DNS query would look
like on our network:
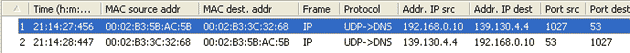
This is
the captured packet we are going to deal with. To
generate this packet, I typed "ping
www.firewall.cx" from
my linux prompt. The command generated this packet,
which was put on my network with the destination
being a name server in Australia. Notice the
Port Destination which
is set to 53, on which
the port DNS works, and
the protocol used for the DNS Query, which is
UDP.
|
